Securing Your Network with Tempest Solutions’ Daily-Updated Pi-hole Blocklists
Since 1997, Tempest Solutions has been at the forefront of of our community. Today, we’re excited to introduce our latest innovation: professional-grade Pi-hole blocklists that update every 24 hours, arming your network with real-time threat intelligence.
Why Real-Time Blocklists Matter
Every day, new phishing schemes, malware distribution sites, and command & control servers emerge—targeting networks both big and small. Outdated defences are like leaving your front door unlocked on a busy street. With our blocklists, you can rest assured that your Pi-hole is equipped with the freshest threat intelligence validated by expert security researchers.
User Benefits Include:
- Peace of Mind Through Precision:
Every domain is rigorously verified by experts, ensuring that legitimate websites remain accessible while harmful domains are blocked. No interruptions to your regular browsing experience. - Proactive Defence, Not Reactive Clean up:
With daily updates, you’re always one step ahead. You don’t wait to be compromised—your network is secured with the most current threat data available.
^Expert verification and proactive updates provide these advantages.
Comprehensive Blocklist Offerings Tailored for You
We believe in marrying robust protection with your specific needs. Choose from our tailored blocklists:
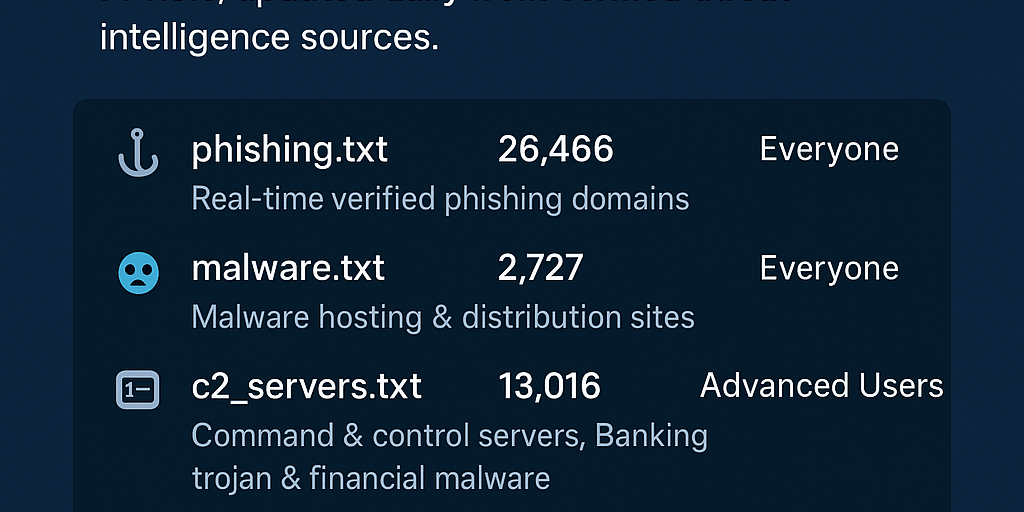
- 🎣 phishing.txt
Real-time verified phishing domains
Count: 26,466 domains
Ideal For: Everyone, to safeguard against deceptive scams. - 🦠 malware.txt
Malware hosting & distribution sites
Count: 2,727 domains
Ideal For: Users seeking an extra layer of protection from malicious payloads. - 🎛️ c2_servers.txt
Command & Control servers, Banking Trojan & financial malware
Count: 13,016 domains
Ideal For: Advanced users requiring enterprise-grade security against financial threats. - 🔒 all_malicious.txt
Complete protection integrating all threat categories
Count: 42,227 domains
Ideal For: Maximum security enthusiasts looking for the most comprehensive defense.
With these specialized lists, you can choose a level of protection that best fits your daily internet usage—whether you’re a casual browser or overseeing a high-risk environment.
User Benefits Include:
- Customizable Protection:
Select the list that meets your security needs. From broad-spectrum protection to targeted defense against specific threats, each list is designed to provide modular security without unnecessary complexity.
^Tailored options allow for flexibility in managing digital security.
Data Sources & Quality: Trust That Matters
Quality is our highest priority. Our blocklists are built on the following key principles:
- Expert Verified: Every domain undergoes meticulous validation by seasoned security researchers.
- Zero False Positives: We rely on strict community consensus to ensure only truly harmful domains are blocked.
- Fresh Intelligence: Our lists refresh every 24 hours—ensuring you’re protected against the most recent threats.
- High Precision: Focus on accuracy means you get robust protection without over-blocking.
- Authoritative Sources: We only integrate data from trusted security organizations.
User Benefits Include:
- Reliability You Can Trust:
Enjoy continuous and quality protection with a system that’s been honed and tested over decades in the industry.
^Our commitment to quality reinforces the trust you can place in our products.
Performance Impact: Security Without Compromise
Effective security should never come at the expense of performance. Our blocklists are optimized to ensure your Pi-hole runs without noticeable slowdowns:
| Metric | Impact |
|---|---|
| Pi-hole Performance | Minimal (~1-2ms per query) |
| Memory Usage | Low (~10-20MB additional) |
| Update Frequency | Daily (automatic) |
| False Positives | Zero (expert verification) |
User Benefits Include:
- Seamless Experiences:
Enjoy enhanced security with minimal system overhead, meaning your day-to-day internet usability remains uninterrupted.
^The metrics demonstrate that you can bolster your security setup while keeping high performance.
Automation That Works for You
Taking care of online security shouldn’t add to your daily tasks. Our system offers seamless automation that ensures continual, hassle-free updates.
Setting Up Automatic Updates
- Edit Your Crontab:
sudo crontab -e - Add this line to update at 2 AM daily:
0 2 * * * pihole -g > /dev/null 2>&1For maximum freshness, consider updating every 6 hours:
0 */6 * * * pihole -g > /dev/null 2>&1 - Verify the Cron Job:
sudo crontab -l | grep pihole
User Benefits Include:
- Set It and Forget It:
Automated updates free you from manual interventions, ensuring your Pi-hole is always armed with the latest threat data.
^ Automation keeps the protection running continuously, addressing evolving threats without extra work on your end.
Trust Tempest Solutions to Empower Your Digital Defences
At Tempest Solutions, we aren’t just about providing tools—we’re about empowering you with continuous, high-quality protection. With a legacy since 1997, our blocklists reflect a deep-rooted commitment to security, precision, and user-centric design.
Explore more about our innovative solutions at Tempest Solutions. Whether you’re a home user or managing a complex network, our daily-updated blocklists offer:
- Peace of Mind and Precision
- Proactive, automated Protection
- Customizable Options for Every User
- Minimal impact on your system’s performance
Together, let’s create a safer digital landscape—one update at a time.